
How You Can Combat SMS Pumping
-
SMS
- 08 Jan 2024
Numerous studies show users prefer getting transactional communications from businesses via SMS more than over any other channel. SMS is secure, reliable, and simple to use. The underlying messaging infrastructure, however, is complex, with multiple players moving messages from your system to recipients’ handsets — and that makes it a potential point of attack for bad actors who want to exploit messaging systems for profit.
Every business should do all they can to avoid fraud, not only to avoid exposure to unnecessary costs, but also to keep criminals from profiting. Fortunately, Plivo provides safeguards you can set on the console and recommends best practices that you can follow in your applications.
Lately we’ve seen an increase in SMS pumping, also referred to as traffic pumping or artificially inflated traffic (AIT). In this type of telecom fraud, bad actors use automated systems to trigger sharp spikes in traffic toward numbers they own and reap a share of the charges generated.
You can take several steps to uncover warning signs that someone might be using your account for SMS pumping:
-
Look for an unnaturally high volume of traffic toward a specific destination or, if you can determine it, a specific mobile network operator (MNO). Compare your current use case traffic with historical data, looking for a large deviation from the expected volumes. That’s suspicious, but it’s not sufficient to establish the spike as fraudulent, as there can be other possible explanations — the app you use messaging to authenticate may have gone viral, for instance, or you may have increased your advertising spend and brought in more users.
-
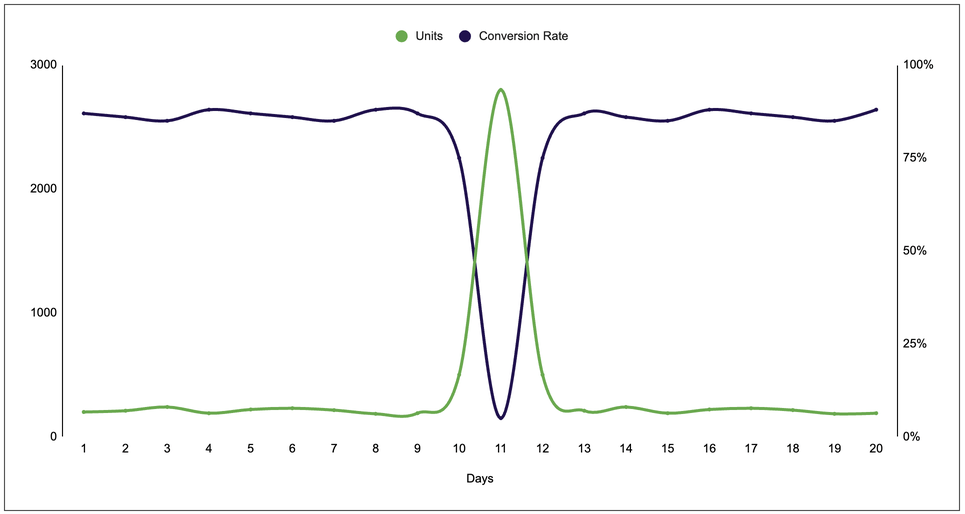
Track conversions from your messaging traffic. Conversion rates that are extremely low compared to the regular patterns are a red flag, but again, not sufficient to establish fraud. You could have a situation where you’re using SMS for logging in new users, for instance, but you’re getting a poor quality of users.
Plivo supports a Conversion Feedback API that lets you track 2FA/OTP login conversions. Since fraudulent traffic makes conversion rates go down (see figure) you can use the Conversion Feedback API to generate real-time alerts.
-
Look for multiple message requests made to the same mobile numbers in a short period of time.
-
Check for messages triggered toward countries to which you’ve never sent messages.
-
Scrutinize logs for spikes of traffic toward blocks of adjacent numbers (+44 3111 111101, +44 3111 111102, +44 3111 111103, etc.).
Best practices for combatting SMS pumping
You can take several steps to make it harder for criminals to take advantage of your account and your phone numbers for SMS pumping.
Our top recommendation is to activate Fraud Shield, Plivo’s new solution designed specifically to fight SMS pumping. Fraud Shield offers two primary features that operate at the destination country level — Fraud Thresholds allow you to control the number of messages that can be sent per hour and Geo Permissions allow you to control the countries to which your SMS messages are sent.
We use several factors to determine the level of risk for each country, including any previous cases of fraud and local regulations. The Plivo team regularly reassesses our risk criteria to ensure that Fraud Shield is using the latest data for recommended thresholds. You can also choose how the system responds to a threshold breach and select who from your team is notified – options include Block & Alert, Alert Only, or Ignore.
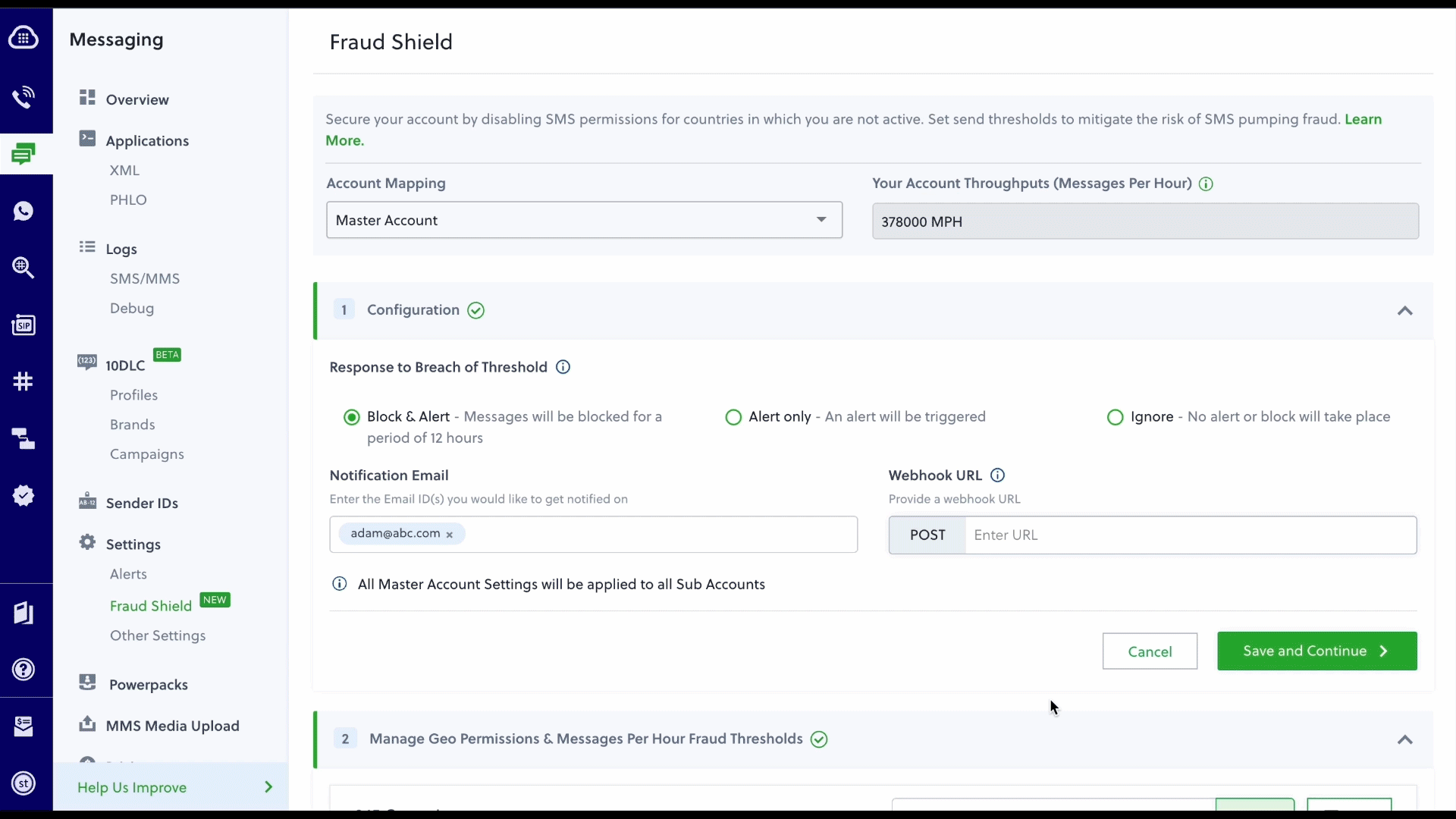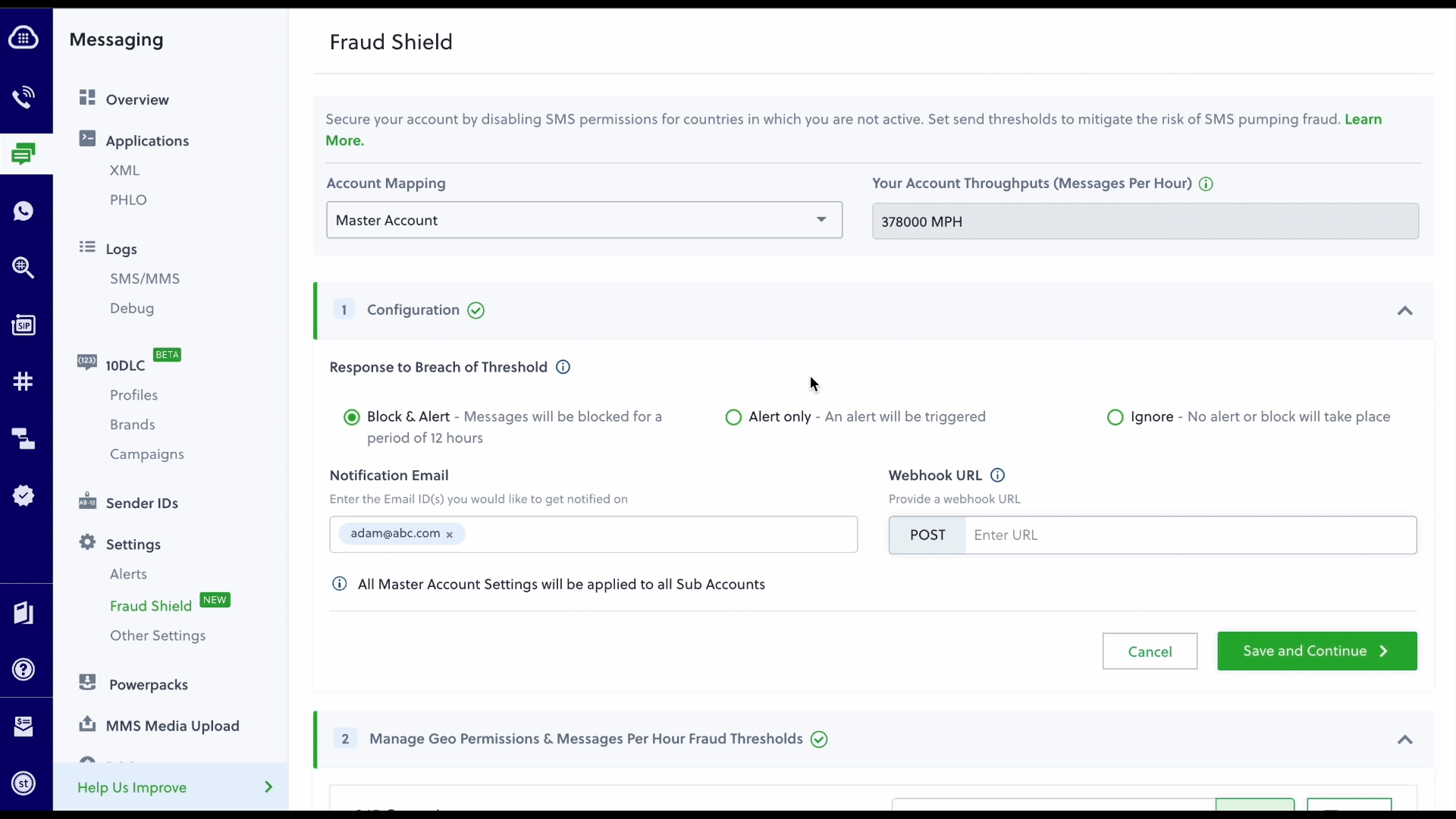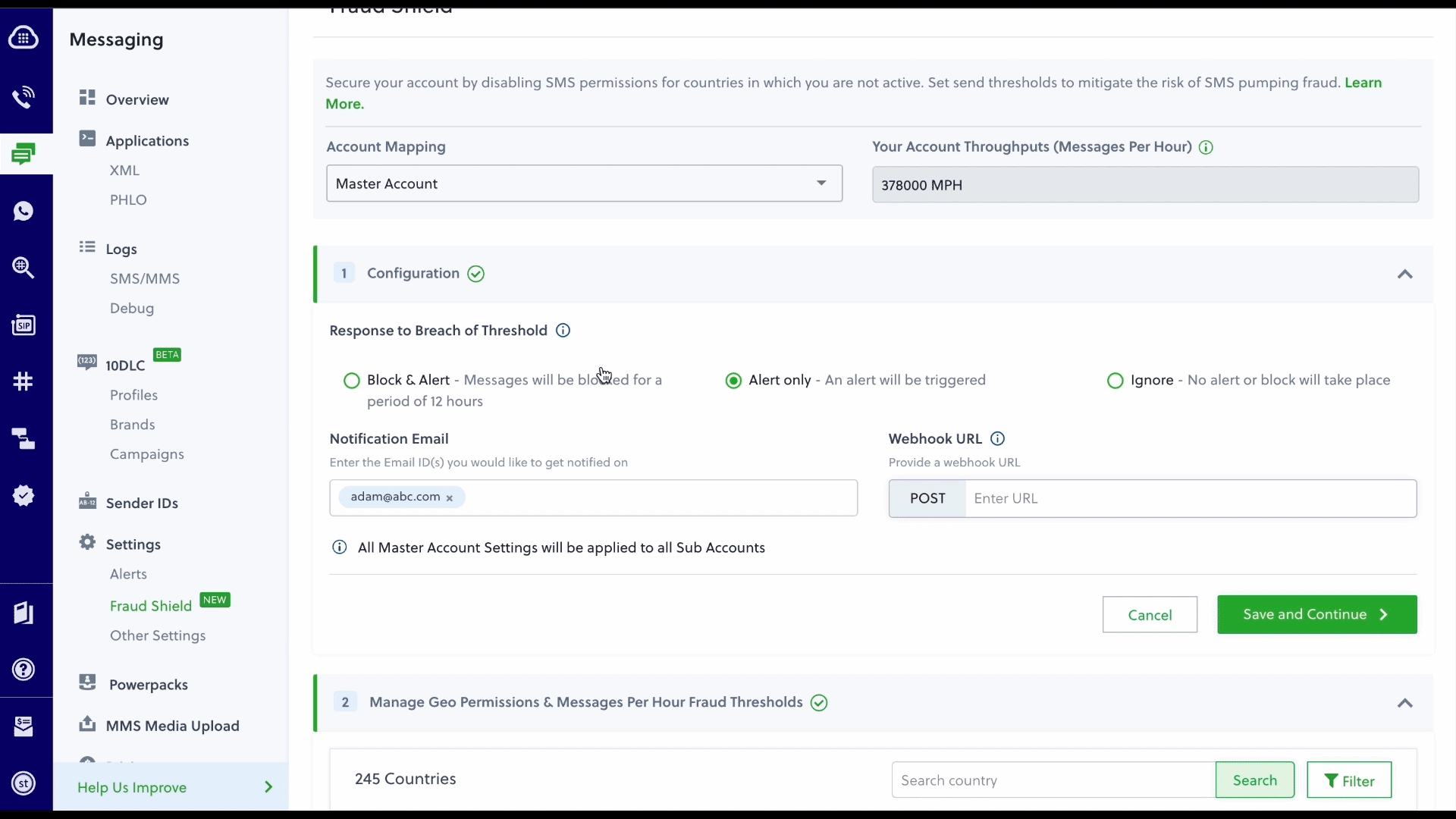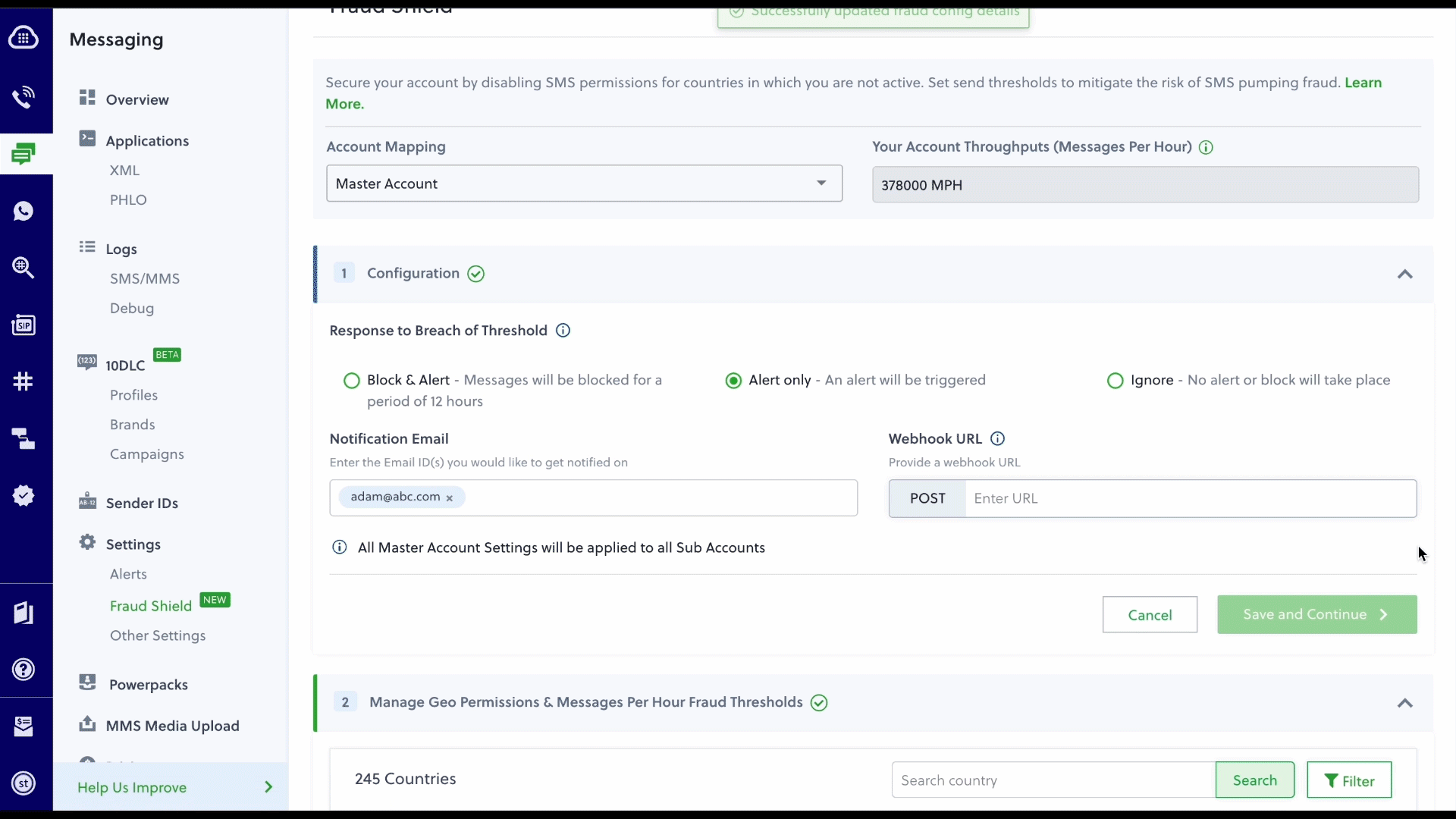
Additional steps to consider depending on your configuration include:
- In your applications, limit the number of messages going out to a destination number based on your use case. For example, suppose you’re sending out one-time passwords (OTP) for two-factor authentication. Most OTP use cases set a duration for which the OTP is valid. During this time, you can block messages triggered toward the destination number. For more generic use cases you can write logic to not send more than n messages per minute or per day. You can also check the source IP addresses for message requests; if hundreds are coming from the same address, fraud may be involved. Consider implementing rate limiting on the source IP address level. Message limitation is use case-dependent, and you’re likely to be the best judge of how to implement it.
- Implement challenge-response verification: Most if not all instances of SMS pumping employ bots that target a series of numbers with as much messaging traffic as possible. For example, if you have a web application, the bots’ scripts will try to register numbers on your login page one after another. To control this behavior you can add challenge-response systems such as CAPTCHAs to your forms or pages to make sure humans and not bots are using them.
- Secure your authentication IDs and tokens. Don’t push code that includes authentication information to public repositories. For mobile applications, follow best practices recommended by the mobile OS.
Winning the battle against telecom fraud
SMS pumping and other telecom fraud waste thousands of dollars for carriers and their customers. Together, you and Plivo can fight telecom fraud and keep your customers — and your colleagues in the finance department — happy.


